VPC Peering allows direct communication between VPCs (inter-region & cross-account) using OSI Layer 3 (Network). Once the VPCs are connected, 2 VPCs can communicate using private IP addresses.
Features
- Instances can connect each other as if they are in the same private network.
- VPC Peers can span AWS accounts and even regions with some limitations.
- Traffic is encrypted.
- Traffic passes via the AWS global backbone.
VPC Peering Limitations
- VPC CIDR blocks cannot overlap.
- The traffic between peered VPCs uses the private IPs.
- The transitive routing is not supported.
- VPC Peering always connects 2 VPCs (Requester and Accepter). The connection cannot be chained.
- ex) When A + B and B + C, A cannot connect to C. The mesh network is required to connect all VPCs.
- No edge to edge routing through a gateway or private connection
- VPC A has an internet gateway
- Resources in VPC B cannot access the internet via the internet gateway of VPC A.
- VPC A has a VPN connection to a corporate network
- Resources in VPC B cannot access the on-premise network via VPN.
- VPC A has a gateway endpoint to S3
- Resources in VPC B cannot access S3 via the gateway endpoint of VPC A.
- VPC A has an internet gateway
Setting up VPC Peering
- You need to start from one VPC (Requester) and request another VPC (Accepter).
- Multi-account & multi-region support
- The peering request should be accepted by the accepter account.
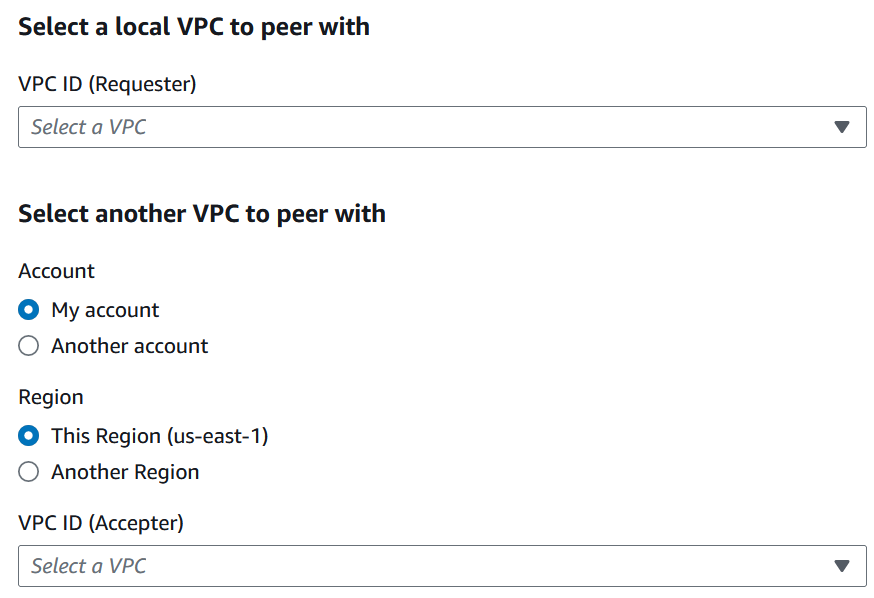
Configuring VPC Peering
- To allow traffic, you need to create a route to the VPC Peering connection in the route table of each VPC.
- You can use NACLs and Security Groups from both VPCs to restrict access.
- In order to resolve public DNS to private IPs, you need to enable and edit DNS settings in the “Peer Connections” menu.
Use cases
- Company mergers, shared services, company and vendor, auditing.
Multi-Region VPC Peering
- Traffic is encrypted.
- Encrypt keys are managed by AWS.
- By default, a query for a public hostname of an instance in a peered VPC in a different region will resolve to a public IP address.
- Route 53 private DNS can be used to resolve to a private IP address with Inter-Region VPC Peering.
- Security groups cannot be referenced across the Inter-Region VPC Peering connection.
- Security groups can be referenced across accounts in the same region among peered VPCs.
- Inter-Region VPC Peering supports IPv6 but cannot be used with EC2-Classic Link.

