There are a couple of ways to connect instances and services in one VPC with other VPCs. – VPC Peering, Open VPC to the Internet, or AWS PrivateLink.
Expose applications and services in a VPC to other VPCs
- Open the VPC to the Internet
- Everything is in public
- Make subnets public
- Not a good idea due to security issues
- Everything is in public
- VPC Peering
- Need to create and manage many peering relationships.
- Management Overhead
- All applications in a VPC are open.
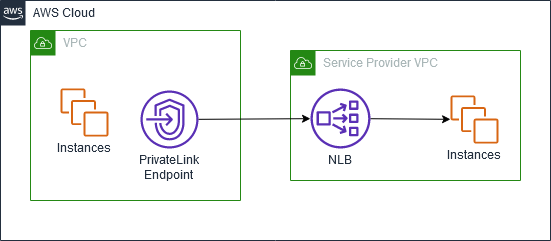
- AWS PrivateLink – Interface Endpoint
- It is the best way to expose a service VPC to many other VPCs.
- It keeps all the network traffic within the AWS network.
- It requires a Network Load Balancer on the service VPC and an ENI(Elastic Network Interface) on the customer VPC.
- It does not require VPC peering, route tables, NAT gateways, nor internet gateways.
Communication between two EC2 instances
- EC2 instances in the same region:
- Traffic stays in the AWS network.
- EC2 instances in the different regions with Inter-Region VPC Peering connection:
- Traffic stays in the AWS network.
- EC2 instances in the different regions WITHOUT Inter-Region VPC Peering connection
- There is no guarantee that traffic stays within the AWS network.
- EC2 instances need to be public.
EC2 instances in one region can communicate with EC2 instances in another region using:
- Inter-Region VPC Peering
- Public IP addresses
- NAT Gateway
- NAT Instances
- VPN Connections
- or Direct Connect connections